
I’ll cut it to the chase from the very beginning: no host can be protected from DDoS attacks very well. But some hosts are DDoS-protected better than others. In this article I’ll explain you why. And I’ll tell you what you can do to protect your online property from DDoS attacks without paying more than you need.
Sucuri WAF ($10-20/mo, great for individual websites and small businesses), CloudFlare ($200/mo plan) for bigger online businesses.
What you will learn
Most non-technical users do not understand the basics of DDoS. This can lead to inadequate decisions or expectations when choosing a host or anti-DDoS solution for a website.
In this article I’ll explain you what you need to know about DDoS in simple words. And this information will be enough for you to understand the DDoS risks and how you will be able to deal with this threat adequately.
Mostly, I’ve written this article for shared hosting users and also for not very technical VPS users. However, it will be useful for anyone interested in this topic.
After reading this article you will know:
- What is DDoS? (even if you are not a technical person)
- Is DDoS a problem of your host or your website?
- Why may hosting charge you for DDoS attacks?
- What you need to know regarding DDoS protection when choosing a hosting?
- Do you really need other DDoS protection in addition to what your host already has?
Anyway, if you want to skip a theoretical part, you can directly go to the practical recommendations.
What is DDoS in simple words
It’s essential to know the basics of what stands behinds DDoS. Understanding this will help you make correct decisions when choosing a hosting and protecting your website from DDoS attacks.
DDoS stands for Distibuted Denial of Service. In more human-like words this means a situation when your hosting’s server or network devices go temporarily out of order because of overloading and stops serving the users.
Here are three types of DDoS attacks. You need to be aware of them to better understand how you and your hosting can deal with them:
- DDoS volumetric attacks (fake traffic flood)
- Protocol-based attacks (malicious traffic affecting the way data is transferred)
- Attacks on specific server or user applications (e.g. WordPress)
DDoS volumetric attacks
This is the most well-known sort of DDoS attacks. When it happens your hosting’s bandwidth gets overflooded by a lot of fake traffic from multiple different sources. As a result your hosting stops serving legitimate users.
Think of a highway to a city. The city represents a hosting. And the highway represents an incoming network cable. Imagine the highway is filled with moving cars. There are lots of vehicles on a highway. The problem is that the vast majority of such vehicles are fake (think of pokemon cars that take up practically all the space on the highway). And the problem is that the whole highway (bandwidth) is occupied by these DDoS pokemon cars leaving no or too little space for the real cars (legitimate traffic).
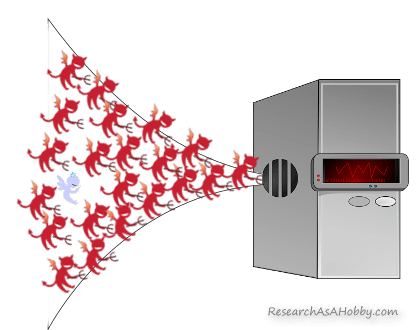
Volumetric DDoS attack: Legitimate users simply can’t get through to the server (and your website)
The problem of dealing with this kind of DDoS attacks is that it’s impossible for a hosting to handle so much increased traffic. Hosting simply can do nothing if a traffic gets suddenly too massive. The network bandwidth is limited and gets overfilled even before getting to the hosting servers.
The fake traffic takes up all the bandwidth whatever wide it is. And almost no legitimate traffic can get through. The websites on the affected hosting become isolated from the the Internet.
So, the problem is not in a particular hosting, but in the Internet network nature.
However, it’s possible to filter out fake and malicious traffic of this kind of DDoS attacks. See about it further in this article.
By the way, a similar DDoS attack effect may take place if for a example a website post gets too viral. Imagine millions of visitors visiting the post simultaneously. In real life it happens not very often. Whereas DDoS attacks initiated with fake botnets (fake visitors) are frequent and become more and more powerful with threatening pace.
DDoS protocol attacks
This type of attacks targets your hosting server resources (RAM, CPU) and communication equipment such as server routers, switches, load balancers, server firewalls. The point of such attacks is that fake requests to the hosting server occupy all connections and do not free the connections up. Or sending too much data and too frequently to the hosting server.
Here’s a human life analogy to understand this kind of DDoS attacks. Imagine a detrimental flash mob when a lot of fake buyers get in a supermarket. They take some goods and go to cashiers intending sort of to pay. But then they get back to the room to take some more stuff. Or they say they can’t find credit cards to pay. The queues get frozen, the cashiers are stuffed with registering the goods which will never be paid. The resources are wasted. Legitimate buyers are not served.
The problem of dealing with such DDoS attacks (mind the the supermarket analogy) is that it’s hard to find out who is participating in a sabotaging flash mob and who is a legitimate buyer.
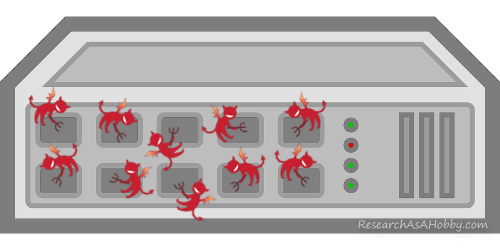
Protocol DDoS attack occupies all connections and increases CPU/RAM load
See further in the article what hosting can do and what you can do against such DDoS attacks.
DDoS attacks on applications
This kind of DDoS attacks exploit weaknesses of applications installed on a server (WordPress, Joomla, Drupal, MySQL, Apache, Windows ISS etc). The result is usually an increase of CPU and/or memory usage.
For example, imagine a malicious bot initiating a lot of search requests through a search field on your website. The problem is that such search operations require a lot of server resources. And even a comparatively low number of search requests may significantly hamper your server and slow down or even take down your server.

Even a small amount of bots targeting weak spots of your website may overheat your server
(For the above image a picture from here was used)
The problem of determining this kind of DDoS attacks is that these attacks often go under radar. Their number may be not noticeable and their activity may seem quite legitimate.
Who is in charge of protecting from DDoS attacks?
That is an interesting question.
DDoS attacks may target not only hosting infrastructure, but also networks (upstream bandwidth; DNS). Also, the root nature of DDoS attacks lies in the nature of the Internet itself (the assaulting capacity of bots will be always more powerful than any hosting can handle).
At the same time, it’s hard to determine who is a bot and who is a legitimate user. Very often the bots parasite on legitimate computers. And the owners even don’t realize that their computers have become zombies generating DDoS attacks.
That’s why the problem of DDoS attacks is not only the problem of a particular hosting or a particular website owner. This is a problem of the whole legitimate Internet community.
And everyone (hosting, website owner, anyone else with a device connected to the Internet) is in charge of protecting from DDoS attacks happening in the Internet.
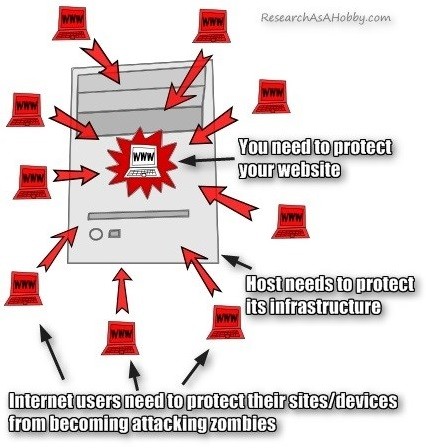
Responsibility for anti-DDoS protection
But what I’ve said above was too general. Now let’s see more practically.
Who will pay for anti-DDoS protection?
It’s simply not possible for a hosting to build a thorough anti-DDoS protection. And even if hosts wanted to, it would cost too much for the businesses (and subsequently for the users).
That’s why hosting companies have really no choice other than focusing on just some of the anti-DDoS protection measures locally on a software level and sometimes on a hardware level. Some hosts which are not the cheapest (e.g. LiquidWeb of other fully managed WP hosts) go further and use expensive hardware to cope with DDoS attacks. These measures can protect hosting to some extent, but more powerful DDoS attack can get through anyway, unless you pay extra like with LiquidWeb.
To mitigate attacks which cause huge traffic and server load, most hosts suggest using services such as CloudFlare, Sucuri WAF and others. These services can mitigate the high-volume and malicious traffic that hosts themselves simply can’t handle or can’t even identify due to technical reasons. As a rule, users have to pay for these services additionally.
So, it turns out that it’s users who pay for DDoS protection. Yes. DDoS affects not only your website, but the whole hosting. And you pay for the services like I’ve mentioned above to protect from DDoS attacks not only your website, but also your hosting.
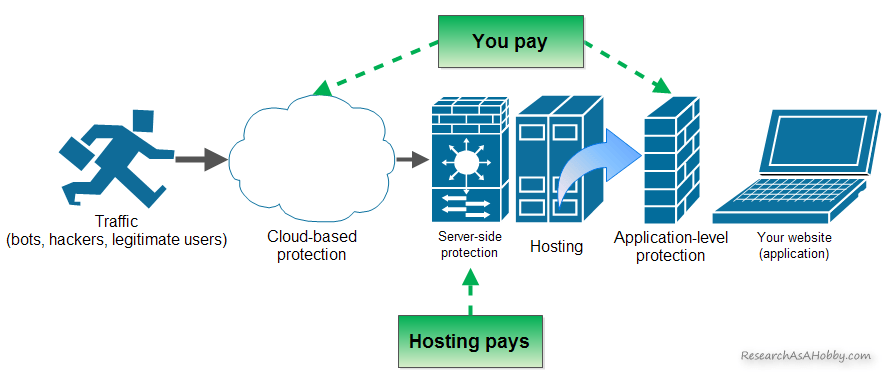
Anti-DDoS and anti-hack protection. Who pays?
“Why to pay for an anti-DDoS protection then if it’s hosting’s benefit?” you may ask. The answer has two aspects:
- With anti-DDoS protection you also get additional anti-hack protection specifically for your website. Sucuri WAF is the leaders in this respect regarding price and quality balance.
- 2. And this aspect is even more important and stays pretty unnoticed. You directly or indirectly bear the responsibility towards your hosting that your website or application will not be the gateway for a DDoS attack. If you use hosting’s services you and your hosting are in one boat (whether you like it or not). Protecting your website from DDoS attacks makes your hosting a safer place. More on that below.
DDoS attack happened. Who will pay for it?
A good shared hosting explicitly or implicitly restrict bandwidth, CPU,RAM even if you use so-called unlimited plan (here’s an example of this good practice). This makes the hosting business safer and the websites performance more stable for all its users.
If there are no such restrictions (e.g. in case of some VPS services) VPS users may even find out that in case of DDoS attacks they have to pay for all the troubles (e.g. huge bandwidth, operations costs of support etc).
If you are on a VPS, make sure with your host what will happen if you get a DDoS attack:
- In many cases your hosts just turns off your server (null routes your IP).
- In some other cases if the attack is not very severe, it just eats all your bandwidth, CPU or RAM limit. And your service get suspended.
- In the worst case (worst for your budget), if your hosting is powerful enough to hold a lot of traffic (caused by the DDoS attack) without restricting your services, you’ll get a bill for all the traffic and server resources spent during the DDoS attack. Someone has to pay.
That’s why you are interested in using special services (Sucuri WAF or CloudFlare etc) that give you protection against DDoS attacks.
As I wrote above, DDoS attack to your website is the problem that affects not just your website, but the whole hosting. Hosting companies lose a lot of money as a result of DDoS attacks (leaving clients, operational costs). Hosting’s brand suffers too.
That’s why if a hosting can identify that your website is the target of the DDoS attack, the easiest what the hosting can do is to take down your website. Technically it’s a null routing (simply to say, canceling) of the IP address that your website has. In this case both your website and other websites on the same IP suffer from downtime. The whole server with shared resources actually suffers from downtime or very slow and unstable performance.
The hosting takes the financial loss initially. But you, as an owner of the targeted website, may also have problems. The hosting may issue you a huge bill for the attack, not to mention no refund for you and a quite long downtime while you sort this out. This happens quite often with VPS users. But shared hosting users are at risk too.
That’s why using anti-DDoS protection for your website or application can save not only the performance of your website, but your money too. Not to mention your nerves and your time.
Choosing a hosting that has some DDoS protection on a hardware level is also advantageous since it allows to mitigate average DDoS attacks without any degrading of performance.
Here’s a table overview of the above thoughts if a DDoS attack happened:
What DDoS attack means for You: Downtime of your website.
What DDoS attack means for Hosting: Costs of high CPU, RAM usage.
What DDoS attack means for You: Your site is slow or not available. Huge bills for wasted bandwidth and CPU usage are possible, if the attack was through your website.
What DDoS attack means for Hosting: Loosing clients, refunds.
What DDoS attack means for You: Loosing traffic, conversions and sales.
What DDoS attack means for Hosting: Angry clients, bad reviews.
What DDoS attack means for You: Your dissatisfied or angry visitors/clients.
What DDoS attack means for Hosting: High operational costs (engineers, client support).
What DDoS attack means for You: Time wasted on waiting or/and efforts trying to find an alternative hosting.
What DDoS attack means for Hosting: Using hardware anti-DDoS protection is expensive, but decreases risks of suffering from attacks on servers and client’s websites.
What DDoS attack means for You: Using cloud-based anti-DDoS protection can be expensive, but it decreases risks of suffering from attacks on your website.
Both server-side protection of hosting and cloud-based anti-DDoS protection of your website in many ways do different parts of the work. So, hosting companies are interested if their clients (including you) use cloud-based anti-DDoS protection. You are interested in cloud-based anti-DDoS protection to decrease the risks of specifically your website being attacked.
Shared hosting with anti-DDoS protection?
Some hosts have anti-DDoS protection only on a software level on their servers. It’s fine for handling small DDoS attacks targeting weaknesses of server software. But this protection measure is not enough. Special hardware is required to handle more serious attacks. But this hardware is expensive and not all hosts can afford it. Being able to handle bigger than average DDoS attacks is pretty costly.
Most hosts do not offer any serious DDoS protection or you need to pay additionally for it. The price for DDoS protection can be significantly higher than the price of your hosting services.
However, even some some shared hosts (which have higher than average prices though) have hardware firewalls which provide protection from not very serious DDoS attacks.
For example, A2Hosting can also mitigate not severe volumetric DDoS attacks (a couple of gigabits per seconds). It’s enough to be on a safe side in many cases. But the protection fails and downtimes are possible if a volumetric DDoS attack is a more serious one (tens of gigabytes per second).
WP Engine is not a shared hosting (it’s a fully-managed host) and it has an advantageous anti-DDoS solution. It utilizes the capacity of Cloudflare powerful network for protection against DDoS attacks. Cloudflare is one of the most powerful solutions against DDoS threats.
Another fully managed hosting that offers an advanced DDoS protection is Kinsta. This hosts utilizes the power of Google Cloud Platform (GCP) Firewall. Apart from an IP-blocking functionality, the host offers a Geo-blocking feature (country-level, state-level, and city-level GeoIP).
In general, shared hosts usually can’t protect from serous volumetric DDoS attacks. The hosts only survive it (which means waiting till the attack ceases with downtime for users). Unfortunately, this is the vulnerability the Internet community has to live with.

Shared hosts can only suggest their users using cloud-based DDoS protection services such as CloudFlare, Sucuri WAF. The services like these can protect you from tens and hundreds of times more powerful volumetric DDoS attacks compared to what protection a single host can provide. Using such services is the right option if your website or application is the actual or possible target for DDoS attacks.
By the way, A2 Hosting partners with Sucuri and has more attractive prices for this security and anti-DDoS protection service.
Anti-DDoS protection using a cloud service
I’ve already mentioned that your website is not protected from any serious DDoS attacks using anti-DDoS protection systems implemented by hosts locally. The reason is simple: hosts do not have network capacity to mitigate volumetric (high-traffic) attacks.
That’s why cloud-based services play an important role in saving your website’s performance and security. And as I’ve noted earlier, hosts are interested if you use an anti-DDoS protection service since it helps to keep the whole hosting’s server in a healthy shape.
That’s why a lot of hosts recommend using CloudFlare (at least a free plan). Let me ponder on this a bit.
Hosting is interested if you use a free CloudFlare plan, because it helps the hosting to avoid comparatively small DDoS attacks. It’s much better for the hosting than if you don’t use any DDoS mitigation service at all.
But at the same time, a free CloudFlare plan is not so quality service (compared to paid alternatives) for you as a website owner, because it may result in a weak user experience of your visitors. In particular, your site may appear not available too often because of CloudFlare.
Also, it happens too often when CloudFlare makes your visitors wait for several seconds before loading your website. You can’t complain for the free service like that, but anyway.
If you use a free plan of CloudFlare, it will be good for your hosting (less risks of DDoS atacks). But it’s not very advantageous for you as a website owner (your visitors get irritated).
Moreover, a real anti-DDoS protection offered by CloudFlare that is comprehensive (can handle layers 3, 4 and 7 attacks) starts from $200/mo. This is a great service for quite a serious price.
If your budget is more limited than a couple of hundred bucks per month, a great solution is Sucuri WAF. For $10-20/mo it can mitigate layer 3, 4 and 7 DDoS attacks. Moreover, it functions as a security solution for your website or application (if you are a WordPress user, you can look at this comparison article).

Cloud-based protection filters out malicious and DDoS traffic to your website
Sucuri WAF can also be used as a caching layer to make your website faster (see my experiments here). It’s like a caching in CDN that makes your site faster.
These features and very affordable pricing make Sucuri WAF the best choice of many bloggers and small online business owners who are not ready to pay several times more. I’m using Sucuri WAF too.
Useful links and further reading
For more information on DDoS attacks and how to protect from them, I suggest looking at the following useful and interesting materials:
- A bit technical but quite comprehensive overview of DDoS attacks types, techniques and defense approaches.
- Internet-of-Things generate DDoS attacks against small online businesses (read the article).
- DDoS and Brute force attacks on WordPress, Joomla, Drupal and vBulletin sites in numbers.
- More about DDoS threat for website owners.
- How your website may be DDoS’ing other websites and you even don’t know about it.
- More detailed and a bit more technical overview of DDoS attacks
Conclusion and practical advice
As a resume, DDoS attacks can be different and always evolving. Moreover, there’s no practically suitable and cost-effective way for any hosting company to protect their servers from serious DDoS attacks.
The targets of DDoS attacks can also be different. DDoS attacks may target businesses, hosting companies, particular websites or applications, particular servers or even a whole sub-network.
That’s why anti-DDoS protection is the responsibility of both hosting clients and hosting providers. And moreover, all Internet users are participating in this problem, because hacked websites or computers can be used as a part of botnets to generate DDoS attacks.
Decent hosting companies have some DDoS protection for any users. But it’s good only for some types of DDoS attacks. Using a hosting with powerful server infrastructure (e.g. WP Engine hosting) gives you more chanced to survive DDoS attacks even without noticing them.
If you use a budget shared hosting and you think that your website is unlikely to be a target for DDoS attacks, then it does not make much sense to use additional anti-DDoS protection. However, you still need anti-hack protection.
If you use a shared hosting or VPS, be aware that DDoS attacks to your hosting will happen sooner or later (and it means downtime and/or poor performance during a several hours or maybe more). In many cases it’s not your hosting’s fault.
However, some hosts have better anti-DDoS protection systems than others by default. From this perspective I like the following hosts (among the ones I generally recommend): LiquidWeb, WP Engine, Kinsta, and also A2Hosting. At the same time, by no means you should consider that hosts (especially more affordable ones) have strong protection against really high-traffic DDoS attacks.
For anti-DDoS protection which can mitigate high-volume attacks you need to use either expensive solutions offered by some premium hosts (like LiquidWeb’s server solution from $99/mo to $499/mo). Or use a cloud-based service for website protection like Sucuri WAF ($10-20/mo), CloudFlare ($200/mo). However note, that cloud-based anti-DDoS protection is not effective, if an intruder knows your website or application original IP address.
For websites on shared hosting or for VPS users Sucuri WAF is the best solution I know. It’s very affordable and really good for its price. But if you have a serious online business then you may want to pay a pair of hundreds dollars monthly to be protected.
P.S.: If your website or application is currently under a DDoS attack or you want to protect your online property, look above.

BTW, I respect your privacy, and of course I don't send spam, affiliate offers or trade your emails. What I send is information that I consider useful.


